
TL;DR
- Geektime reported that one Cyber Security Specialist discovered that he was able to access his neighbors’ VoIP data.
- You can determine whether your fiber optic network exposes your sensitive information to neighbors, depending if your ISP supplies a PON or P2P architecture.
- If it’s GPON, the fiber optic cables are set up in such a way that your neighbors can learn private details about your VoIP calls and even listen to recordings of the conversations.
- You can take security measures to safeguard your data and ensure that your internet calls are protected regardless of your ISP’s fiber optic infrastructure.
Read the whole article to learn how you can protect your data.
Like businesses across all industries, internet service providers (ISPs) always look for more cost-effective, efficient ways to supply their services to customers. With the introduction of Passive Optical Networks (PON) in the late 1980s, forward-thinking suppliers identified an enormous potential.
Nowadays, ISPs worldwide, like Huawei, Nokia, and Calix, harness the most popular iteration of this point-to-multipoint network technology. Unfortunately for their customers, this Fiber to the Home (FTTH) connectivity method does not come without risks, which can be especially harmful to VoIP users.
Indeed, as Geektime reports, one Cyber Security Specialist recently discovered that his ISP, supplying a PON connection, allowed him to access extensive VoIP calling data of his neighbors. Because of the GPON infrastructure, he could obtain details such as call initiation and hangup time, whether a call was answered, and even snippets of a conversation.
What Is GPON and How Does It Work?
GPON is one of the latest versions of PON technology. The ‘G’ stands for ‘Gigabit,’ referring to its maximum internet speeds. This network infrastructure uses optical fiber cables that transmit data from one point to several other points, hence “point-to-multipoint.”
It has three main components responsible for sending and receiving the necessary signals: an Optical Line Terminal (OLT), a passive splitter, and an Optical Network Unit (ONU device).
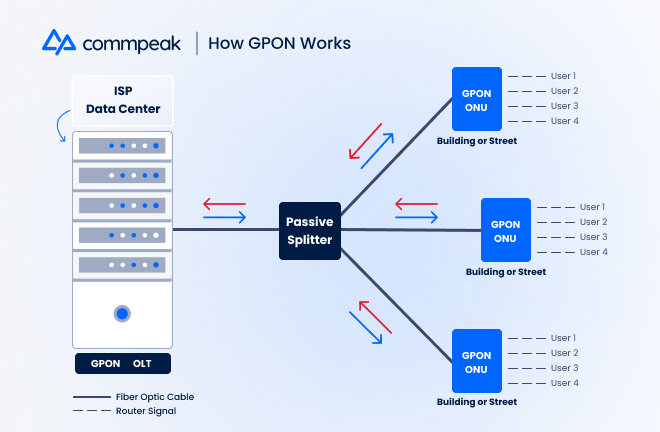
To deliver internet to end-users, the OLT sends a signal through a fiber optic cable to the passive splitter, located anywhere up to 20 km (12.4 m) away. Next, the GPON splitter accepts the signal and divides it into multiple ones, up to 64, sending them through to various cables.
Finally, these signals arrive at GPON-specific ONU devices situated in offices, residential buildings, or streets in single-home residential areas. Users plug their routers into this ONU device, enabling them to connect to WiFi. From there, consumers can work from home, stream content, and make calls over the internet.
What is P2P and How Does It Work?
The other major FTTH architecture ISPs leverage nowadays is point-to-point (P2P). Like GPON, a classic P2P network begins at an Optical Line Terminal, located in the ISP’s main headquarters or one of its data centers.
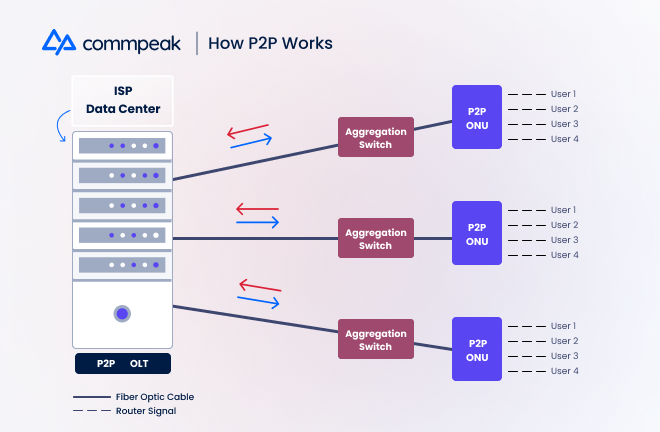
However, unlike GPON, the fiber optic cable connects to an aggregation switch, typically much closer to the user’s premise. The switch directly links to the premise’s Optical Network Unit device, giving each neighborhood or building its own dedicated connection and bandwidth. Users connect to the ONU with their routers, granting them internet access.
Why ISPs Choose the GPON Infrastructure
Both GPON and P2P provide high-speed internet access to end users, but many ISPs are opting for GPON because of its less complex architecture and cheaper maintenance costs.
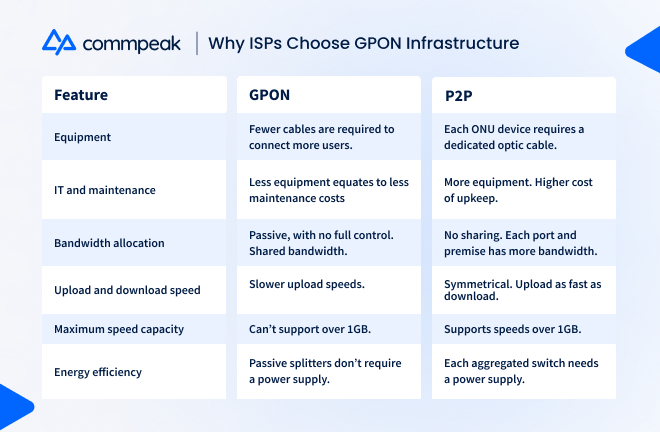
Ultimately, each of these factors leads to lower operational costs for the ISP. Despite its drawbacks, GPON connects to many more buildings and localities, minimizing the resources needed to supply coverage to a more considerable amount of end users.
How Your Neighbors Can Access Your VoIP Data With GPON
GPON ONUs do not have a dedicated line connecting them back to the ISP, making the entire system much less complex than P2P. However, this simplification precisely inspired the previously mentioned security researcher, Elad Ernst, to explore the system’s potential vulnerabilities.
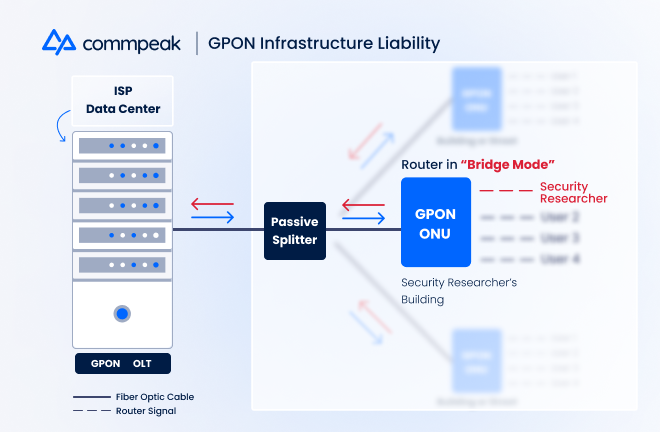
Ernst discovered that his router transformed into a switch on the fiber network by changing its setting to ‘bridge mode.’ Allowing it to function as a DHCP server, he then could request and receive critical data such as the MAC addresses of the other routers on the same fiber.
At that point, the researcher spoofed his MAC address to match those neighbors connected to the same GPON ONU device. While digitally misrepresenting his identity, Ernst skirted around the architecture’s encryption protocols and retrieved enormous amounts of data from other routers.
Sharing his findings on Twitter, he was appalled that he was able to find such a blatant security flaw. In his opinion, the “icing on the cake” was that the provider didn’t bother to encrypt the VoIP calls. Ernst gathered extensive communication data from his neighbors’ devices, theoretically containing extremely sensitive, personally identifying details.
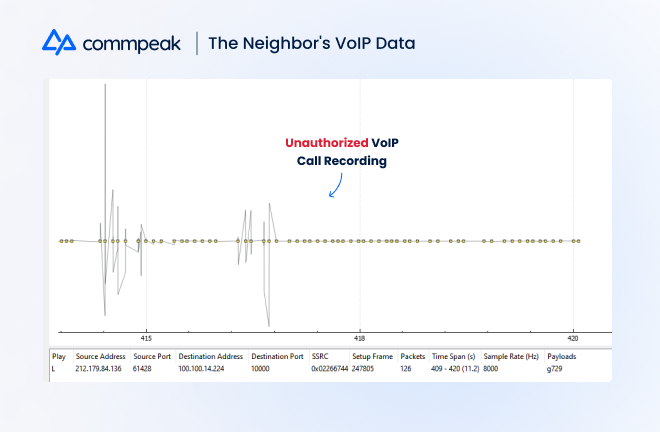
How to Guarantee Your VoIP Calls Are Protected With GPON
To be clear, not every ISP’s GPON infrastructure has that critical security defect that Ernst detected. Nevertheless, it is much better to be safe than sorry about your VoIP data. Choosing a VoIP provider that supports SRTP and SIP-TLS for SIP trunking helps ensure this protection.
Two standard protocols are employed when initiating and establishing a VoIP call: SIP (Session Initiation Protocol) and RTP (Real-time Transport Protocol). SIP creates the connection, and RTP transmits the data. As relatively straightforward protocols, anyone with a basic understanding of network technology can procure its relevant insights.
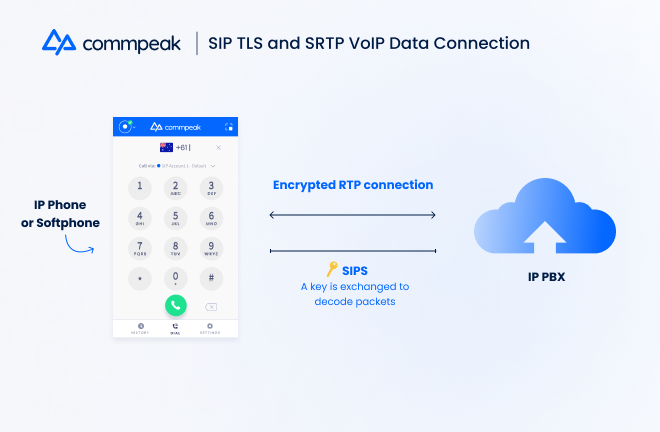
In response, VoIP developers created encryptions for these protocols, protecting them against hackers. SIP-TLS (Transport Layer Security) or SIPS (SIP Secure) ensures that a VoIP call can establish a secure connection. SRTP (Secure RTP) encodes VoIP data into packets that can only be decrypted by a unique key sent to the receiver via SIPS.
Another simple solution to the GPON architecture dilemma is to adopt a VPN Gateway service. The VPN creates a private tunnel for your data, encrypting it against nosy neighbors that want to spy on you.
Safeguard Your VoIP Data With Secure Calling Solutions
With forecasters predicting that the GPON market will triple by 2028, end-users, particularly those who regularly make and receive internet calls, need to be increasingly aware of the potential of their network’s vulnerabilities. At least one ISP was discovered to have ignored GPON’s inherent security flaw, and you should expect there are others out there.
When selecting a VoIP provider, it’s best practice to choose a company like CommPeak that employs end-to-end SRTP and SIP-TLS encryptions for all SIP calls. You’ll never have to worry about your neighbors snooping in on your communications again.
Sign up today for a free trial and start experiencing higher-quality, fully-secure VoIP connections.
Sources:
- Admin. (2022, July 6). Everything about GPON (gigabit passive optical network). STL Blog. Retrieved August 15, 2022, from https://www.stl.tech/blog/everything-about-gpon-gigabit-passive-optical-network/
- Aleksalsi, O. (2022, August 4). Do you have fiber internet? You may be “sharing” information with the neighbors. Geektime | News. Retrieved August 15, 2022, from https://www.geektime.co.il/israeli-researcher-finds-security-flaw-in-gpon-fiber-optic/
- Ernst, E. (2022, August 3). Icing on the Cake. Twitter. Retrieved August 15, 2022, from https://twitter.com/EladErnst/status/1554959199481864192
- GPON market trends 2022-2028: Global Forecast Report. Global Market Insights Inc. (n.d.). Retrieved August 15, 2022, from https://www.gminsights.com/industry-analysis/gigabit-passive-optical-network-equipment-market
- Taylor, R. (2021, May 14). MAC address vs IP address: What’s the difference? BlueCat Networks. Retrieved August 15, 2022, from https://bluecatnetworks.com/blog/mac-address-vs-ip-address-whats-the-difference/
- What is SIPS and SRTP? Askozia. (2020, November 27). Retrieved August 15, 2022, from https://askozia.com/voip/what-is-sips-and-srtp/
- Wikimedia Foundation. (2022, August 9). Voice over IP. Wikipedia. Retrieved August 15, 2022, from https://en.wikipedia.org/wiki/Voice_over_IP
Ready to SeeCommPeak in Action?
Book a DemoRelated Articles

What is a Shared Inbox? The Key to Taming Omnichannel Chaos
